In a world where cyber threats are becoming increasingly sophisticated, protecting your business from potential attacks is more important than ever. The Essential 8 Framework, developed by the Australian Cyber Security Centre (ACSC), provides a set of recommended strategies that can help organisations minimise their exposure to cybersecurity risks. In this blog post, we’ll explore what the Essential 8 Framework is, why it’s critical for your business, and how you can implement these strategies to bolster your cyber defences.
What is the Essential 8 Framework?
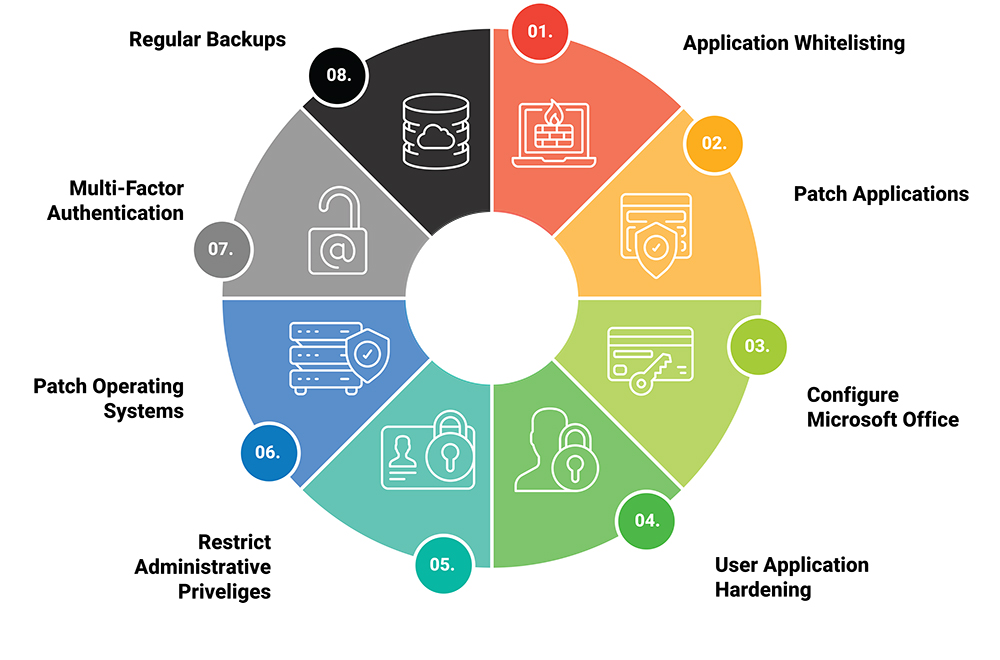
The Essential 8 Framework is a set of eight mitigation strategies designed to help businesses strengthen their cybersecurity posture. These strategies are considered the most effective ways to protect against a range of cyber threats, including ransomware, phishing, and other forms of malicious activity. By implementing the Essential 8, businesses can significantly reduce the likelihood of a successful cyber attack and minimise the impact of any incidents that do occur.
The Essential 8 Strategies
- Application Whitelisting:Application whitelisting ensures that only approved software can run on your systems. By restricting what can be executed, you can prevent malicious programs from running and protect your business from harmful software.
- Patch Applications: Regularly updating and patching applications is crucial for closing security gaps. Unpatched software is one of the most common ways cybercriminals gain access to systems. Ensure all software, including third-party applications, is kept up to date.
- Configure Microsoft Office Macro Settings: Macros in Microsoft Office can be a vector for malware. By configuring macro settings to block macros from the internet and only allow those from trusted locations, you can reduce the risk of a macro-based attack.
- User Application Hardening: This involves disabling or restricting certain features within applications that are commonly exploited by attackers, such as Flash and Java. Hardening your applications makes it more difficult for cybercriminals to find and exploit vulnerabilities.
- Restriction Administrative Privileges: Limiting administrative privileges reduces the potential damage that can be caused if an attacker gains access to an account. Only give administrative access to users who absolutely need it, and regularly review and update these permissions.
- Patch Operating Systems: Just as with applications, operating systems need to be regularly updated and patched to protect against vulnerabilities. Ensure that your business uses supported operating systems and that they are patched promptly.
- Multi-Factor Authentication: MFA adds an extra layer of security by requiring users to provide two or more forms of identification before accessing systems. This greatly reduces the likelihood of unauthorised access, even if passwords are compromised.
- Daily Backups: Regularly backing up important data ensures that your business can recover quickly in the event of a cyber attack, such as ransomware. Backups should be stored securely and tested regularly to ensure they can be restored when needed.
Benefits of Implementing the Essential 8
- Reduced Risk: By following the Essential 8, you can significantly lower the chances of a successful cyber attack on your business. These strategies address common vulnerabilities and provide a solid foundation for cybersecurity.
- Cost Effective Security: Implementing the Essential 8 doesn’t require a huge investment. Many of the strategies are relatively simple to deploy and can be managed in-house with the right expertise.
- Compliance: For many industries, adhering to cybersecurity frameworks like the Essential 8 is necessary for regulatory compliance. By implementing these strategies, your business can meet industry standards and avoid potential fines or legal issues.
- Enhanced Reputation: A robust cybersecurity posture demonstrates to customers and partners that your business takes data protection seriously. This can enhance your reputation and build trust with stakeholders.
Best Practices for Implementing the Essential 8
- Priorities Strategies: Not all strategies may be immediately feasible for your business. Start by implementing the most critical strategies first, such as application whitelisting and patch management, and work your way through the list.
- Regularly Review and Update: Cyber threats are constantly evolving, so it’s important to regularly review and update your security measures. Ensure that your implementation of the Essential 8 is kept up to date with the latest best practices.
- Engage with Experts: If your business lacks the in-house expertise to implement the Essential 8 effectively, consider engaging with cybersecurity professionals. They can provide guidance and support to ensure your business is well-protected.
- Educate your Team: Cybersecurity is everyone’s responsibility. Make sure your employees understand the importance of these strategies and are trained to recognise potential threats, such as phishing attacks.
Conclusion
The Essential 8 Framework is a powerful tool for businesses looking to protect themselves against the growing threat of cyber attacks. By implementing these eight strategies, you can significantly reduce your exposure to risks and ensure your business is well-defended against potential breaches. Don’t wait for a cyber attack to happen—take action now to secure your business and safeguard your valuable data.