AI-Powered Phishing Simulation
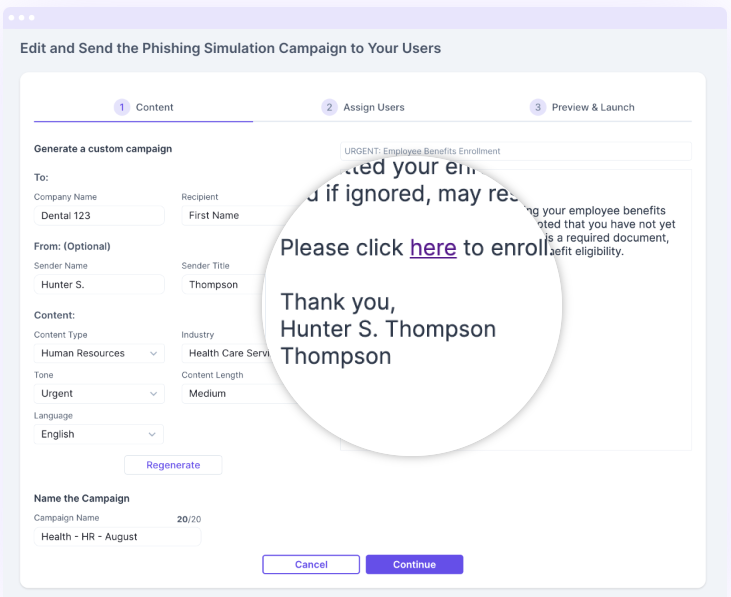
Embracing Innovative Anti-Phishing Solutions
White Rook Cyber breaks the mold of traditional static libraries, providing dynamically tailored content for each department. This cutting-edge approach allows you to gather detailed data reports, highlighting the individuals who successfully identified the phishing attempts and those who failed to do so.
By staying up-to-date with the latest phishing trends, we ensure highly accurate simulations, arming your employees against emerging threats.
All our Cyber Packages include a comprehensive Email Phishing Simulator, and our Cyber Team sends random pishing emails to your staff to test there vigilance and responses.
Common Phishing Attacks We Prepare You For
Hackers use this targeted form of phishing to gather information about businesses to draft personalised and convincing messages that are more likely to succeed.
Hackers use this tactic to manipulate individuals into divulging confidential information or performing actions that may not be in their best interest.
Security is a team sport, it's not just the responsibility of security and IT experts but requires all employees to understand the risks and how to avoid pitfalls.
Phishing emails, imitating trusted sources, aim to trick recipients into giving away sensitive information by clicking on harmful links or downloading infected attachments.
These attacks, aimed at senior executives within businesses, seek to trick them into revealing sensitive information or conducting major money transfers.
Malicious downloads from risky websites, deceptive emails, or pop-up ads, can harm a business's system once unknowingly downloaded and opened by users.
Holistic Protection. Hassle-Free. Cost-Effective.
Let us help you take your Cyber Security to the next level!
Our Managed Cyber Security Service Includes:
Why Choose Us?
In today’s digital landscape, robust cyber security is not just a necessity but a strategic advantage. At White Rook Cyber, we offer a comprehensive suite of services designed to protect, detect, and respond to threats with precision and agility.
Our 24/7 Security Operations Center (SOC) and SIEM services ensure real-time threat detection and response, leveraging advanced technologies and seasoned experts to keep your systems secure.
Our Governance, Risk, and Compliance (GRC) audits help you navigate complex regulatory environments and strengthen your security posture with actionable insights and tailored strategies.
With our Penetration Testing, Red Team, and Purple Team engagements, we simulate sophisticated attacks to identify and address vulnerabilities before malicious actors can exploit them.
We understand that every organisation is unique. Our solutions are tailored to meet your specific needs, ensuring maximum protection and compliance while minimizing disruption to your business operations.

Testimonials
Viktor Vukovic
“Partnering with White Rook Cyber we can proactively plan and undertake necessary cyber security assessment and testing activities to safeguard sensitive information and organisational integrity. This partnership has helped us to develop an appropriate roadmap for our business that enables us to understand our current state against an industry recognised cyber security framework. While assisting us to prioritise targeted strategies effectively to achieve our desired level of security maturity”
We Are Here to Help!
Secure your digital world with our expert cyber security solutions. Contact us today to protect your business from online threats.
Send Us Message
Let us know how we can help!









