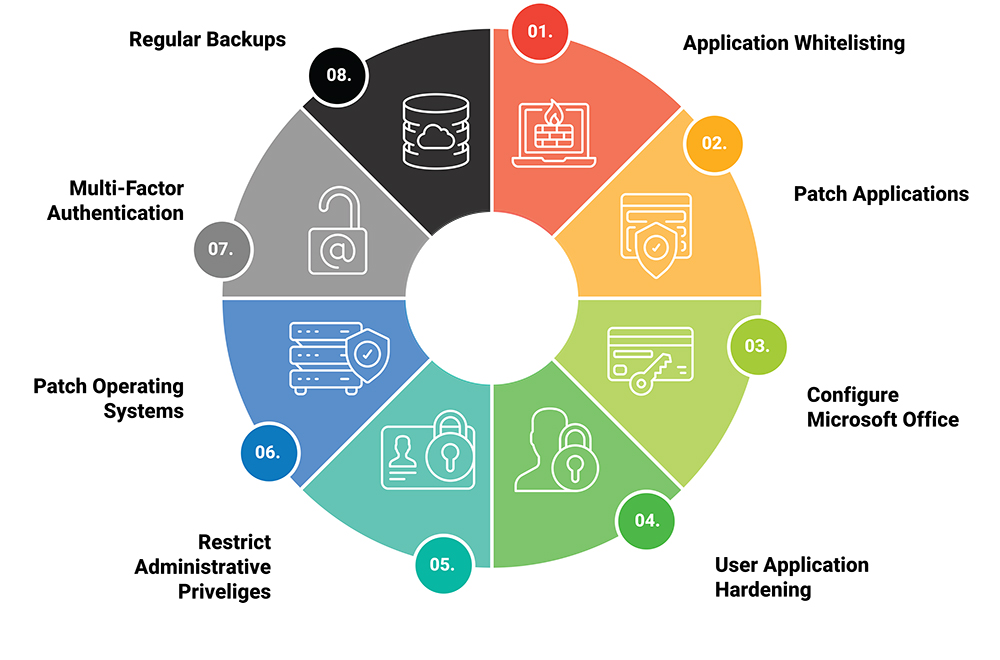
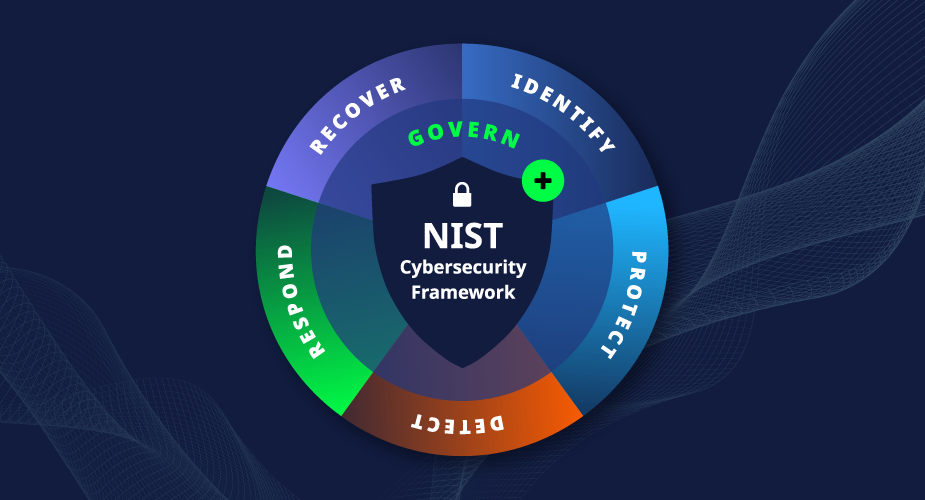
In the constantly evolving world of cybersecurity, staying ahead of potential threats requires a proactive approach. Two popular offensive security strategies, Red Teaming and Purple Teaming, offer businesses the opportunity to test and improve their defences against cyber threats. But which one is right for your organisation? In this blog post, we’ll explore the key differences between Red Team and Purple Team strategies, their benefits, and how to decide which approach best suits your business needs.
What is Red Teaming?
Red Teaming is an offensive security practice where a group of skilled ethical hackers (the Red Team) simulates real-world attacks on your organisation’s systems, networks, and applications. The goal is to identify and exploit vulnerabilities, testing your defences in the same way a malicious attacker would. Red Teaming goes beyond standard penetration testing by using creative and unconventional methods to bypass security measures.
Key Characteristics of Red Teaming:
- Adversarial Approach:
- Focus on Realism:
- Comprehensive Testing:
Benefits of Red Teaming:
- Identifies Hidden Vulnerabilities:
- Test Incident Response:
- Enhances Security Posture:
What is Purple Teaming?
Purple Teaming is a collaborative approach that combines the strengths of both Red Teams and Blue Teams (the defenders). Unlike traditional Red Teaming, where the focus is on simulating attacks, Purple Teaming involves a more cooperative process. The Red Team and Blue Team work together throughout the engagement, sharing knowledge and insights to improve the organisation’s security posture.
Key Characteristics of Purple Teaming?
- Collaborative Approach:
- Focus on Continuous Improvement:
- Balanced Offence and Defense:
Benefits of Purple Teaming:
- Improves Communication:
- Accelerates Learning:
- Customised Defence Strategies:
What Strategy is Right for You?
Choosing between Red Teaming and Purple Teaming depends on your organisation’s goals, resources, and current security maturity. Here are some factors to consider:
- Security Maturity:
- If your organisation already has a well-established security programme and wants to rigorously test its defences, Red Teaming may be the right choice. It’s ideal for organisations that are confident in their basic security measures and are looking to challenge their systems with advanced attack simulations.
- If your organisation is still developing its security capabilities or wants to improve the collaboration between offensive and defensive teams, Purple Teaming might be more appropriate. It provides a learning-focused approach that helps both teams grow together
2. Resources:
- Red Team engagements typically require more time and specialised skills, making them more resource-intensive. If your organisation has the budget and expertise to support a full Red Team exercise, it can provide deep insights into your security vulnerabilities.
- Purple Teaming is often more resource-efficient as it leverages the existing capabilities of both teams. It’s a good option if you’re looking for a balanced approach that maximises the use of your current resources.
3. Objective:
- If your primary objective is to uncover hidden vulnerabilities and test your incident response under realistic conditions, Red Teaming is likely the better option.
- If your goal is to foster collaboration, improve security practices in real-time, and develop a more integrated security strategy, Purple Teaming offers a more comprehensive approach.
Conclusion
Both Red Teaming and Purple Teaming offer valuable ways to enhance your organisation’s cybersecurity. Red Teaming provides a rigorous and adversarial approach that tests your defences under real-world conditions, while Purple Teaming promotes collaboration and continuous improvement between offensive and defensive teams. Ultimately, the choice between these strategies depends on your organisation’s specific needs and goals. By carefully considering your security maturity, resources, and objectives, you can select the strategy that best aligns with your business and ensures robust protection against cyber threats.